Getting Started
If you are starting your journey with Secure60 we have some simple tips to help you get the most out of the platform.
We’ll outline below a standard approach that customers take to enable Secure60 - this approach is designed to deliver value fast and then let your configuration and integration grow over time.
Implementation Approach
Secure60 is design to be simple to implement and improve your cyber security coverage fast.
The below diagram shows our recommended approach to enabling Secure60 within you organisation.
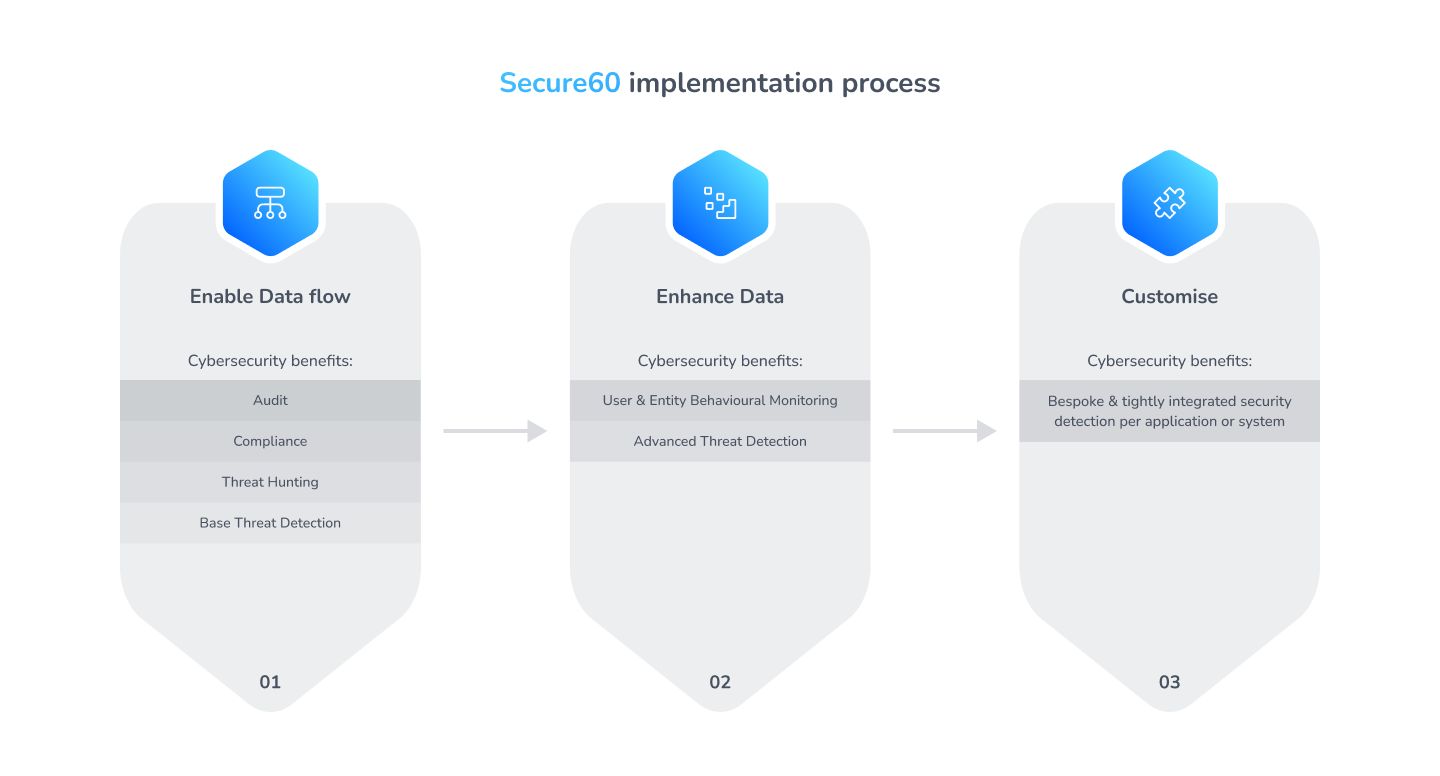
Implementation Guides:
- Enable Data Flow - Get your Event data flowing into Secure60, this achieves a number of key goals for your organisation - audit and compliance is now solved, Threat hunting and basic Threat detection.
- Enhance Data - In this phase you ensure your key Events align to the Secure60 schema, this insantly achieves advanced Threat Detection methods such as user and entity behavioural monitoring (UEBA).
- Customise - This phase is where you identify key / critial applicaitons / services in your organisation and configure custom configurations within Secure60 to ensure wholistic modelling and deep behavioural analysis of acticity within your environment
For additional assistance, please touch base with our support and onboarding team who are happy to help with any implementation questions, scenarios or issues.
Other Guides
We have a number of guides available which show you step by step how to achieve key objective with the platform.
Our recommended starting guides for new users are: